As cyber threats intensify and evolve, the regulatory expectations for financial institutions continue to grow. Historically, banks and credit unions in the United States have relied on the FFIEC Cybersecurity Assessment Tool (CAT) as a benchmark for assessing and managing cybersecurity risks. However, with the FFIEC announcing the retirement of the CAT by August 31, 2025, financial institutions must pivot to alternative frameworks.
The Federal Financial Institutions Examination Council now recommends several robust alternatives: the NIST Cybersecurity Framework, CISA Cybersecurity Performance Goals, CIS Critical Security Controls, and most notably for the financial sector, the Cyber Risk Institute (CRI) Cyber Profile. Developed specifically for financial services organizations, the CRI Profile offers a harmonized, scalable, and detailed approach to evaluating cybersecurity and resilience. This article examines the CRI Profile in depth—highlighting its structure, enhancements in version 2.1, and how it supports compliance and operational strength.
Read the NETBankAudit CRI Cyber Profile Whitepaper
What Is the CRI Cyber Profile?
The Cyber Risk Institute (CRI) is a nonprofit coalition of financial institutions and trade associations that developed the CRI Profile as a standardized cybersecurity assessment model. It addresses the growing need for a unified risk assessment approach amid overlapping global regulatory frameworks.
The CRI Profile simplifies the complexity of overlapping regulatory frameworks by mapping more than 2,500 regulatory expectations into one actionable tool. Built upon the NIST Cybersecurity Framework and ISO/IEC 27000 standards, it allows institutions to conduct meaningful cybersecurity assessments while staying aligned with examiner expectations.

Core Components and Structure
Key elements of the CRI Profile include:
- Alignment with Global Standards: Built on the NIST Cybersecurity Framework (CSF) and the ISO/IEC 27000 series, the Profile consolidates over 2,500 regulatory requirements into a structured and actionable framework.
- 318 Diagnostic Statements: These statements serve as the core of the Profile, providing granular control-level questions that organizations use to assess maturity and risk posture.
- Scalability Through Impact Tiering: Through its Impact Tiering Questionnaire, the Profile adjusts to the size, complexity, and criticality of an institution. The four tiers include:
- Tier 1: National/Super-National Impact
- Tier 2: Subnational Impact
- Tier 3: Sector Impact
- Tier 4: Localized Impact (e.g., community banks)
Enhanced Framework Functions
In addition to the five NIST CSF functions (Identify, Protect, Detect, Respond, Recover), the Profile introduces:
- Govern: Addresses strategic oversight, risk appetite, and governance functions
- Extend: Focuses on third-party and supply chain risk management
Each function is broken into categories and subcategories that map to the diagnostic statements. For example, within the "Govern" function, subcategories include organizational mission alignment, stakeholder risk expectations, supply chain oversight, and independent audit functions.
These features make the CRI Profile not only comprehensive but also adaptable, enabling institutions to perform assessments that are both regulator-aligned and tailored to operational realities.
Key Enhancements in CRI Profile Version 2.1
Released in April 2025, CRI Profile Version 2.1 significantly enhances financial institutions' compliance capabilities while maintaining framework stability. Here's what banking compliance officers and IT security teams need to know:
Foundational Diagnostic Framework Maintained
- All 318 Diagnostic Statements Preserved: Financial institutions already using Version 2.0 can seamlessly transition without disrupting existing compliance processes
- Continuous Assessment Structure: Maintains the proven assessment methodology while introducing valuable enhancements
Comprehensive Regulatory Coverage Expansion
- Enhanced Regulatory Mapping Library: Now includes nearly two dozen additional regulatory frameworks, including:
- Complete FFIEC Development Handbook integration
- CIS Critical Security Controls v8.1 comprehensive mapping
- Full NIST 800-53 Revision 5 correlation
Revolutionary Evidence Collection System
- 100+ Structured Evidence Packages: Dramatically simplifies audit preparation with categorized "Examples of Effective Evidence"
- Efficient Documentation Process: Enables streamlined evidence gathering, reducing compliance burden and audit preparation time
- Clear Compliance Demonstration: Helps institutions confidently demonstrate adherence to multiple regulatory requirements
Expert Implementation Resources
- Updated CRI Profile Guidebook (April 2025): Provides detailed interpretation of all diagnostic statements
- Practical Assessment Tools: Includes specific examples, evidence collection guides, and evaluation criteria
- Consistency Framework: Ensures uniform assessment whether conducted internally or by third-party auditors
CRI Profile Core Functions and Diagnostic Statements
The CRI Profile expands upon the NIST CSF by organizing cybersecurity controls into seven distinct functions: Govern, Identify, Protect, Detect, Respond, Recover, and Extend. Each function includes categories and subcategories that house one or more diagnostic statements used for institutional assessment. These statements allow institutions to evaluate the design and effectiveness of their cybersecurity controls and determine their operational maturity.
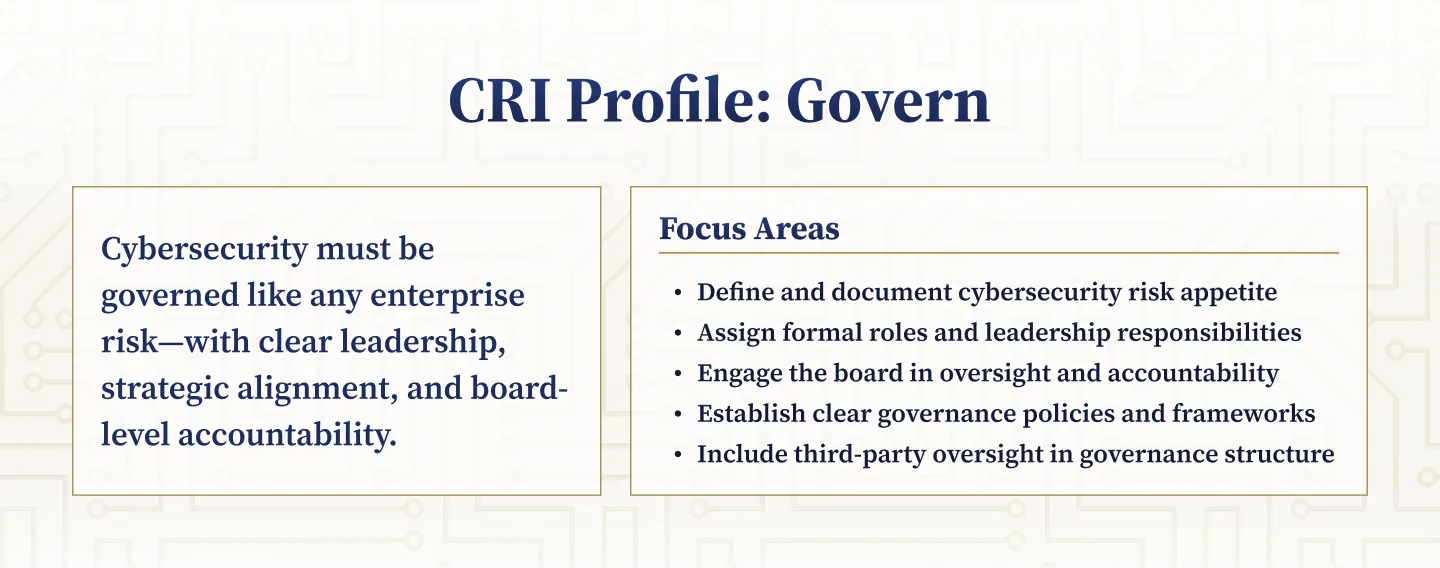
Govern: Strategic Alignment and Oversight
Governance sets the tone for cybersecurity at the institutional level. This function ensures that cybersecurity isn’t treated as an isolated IT issue but as a central component of enterprise risk management. Leadership must be accountable, roles clearly defined, and policies enforced consistently.
- Define and document the institution’s risk appetite
- Assign roles and responsibilities for cybersecurity governance
- Engage executive leadership and boards in oversight
- Implement formal governance policies and procedures
- Oversee third-party and vendor risk exposures at a strategic level

Identify: Visibility into Assets and Risks
Institutions must know what assets they own, where risks exist, and how to track changes over time. This function provides the foundational knowledge needed to understand exposures and prioritize controls. It supports decision-making across all other cybersecurity activities.
- Maintain current hardware, software, and data inventories
- Identify internal and external threats
- Conduct ongoing risk assessments
- Recognize vulnerabilities before they’re exploited
- Use risk insights to adjust security priorities

Protect: Preventive Security Measures
Protective measures reduce the likelihood that vulnerabilities will be exploited or systems compromised. These safeguards cover a wide range of technical and procedural actions and are essential for preserving confidentiality, integrity, and availability.
- Manage identity access and enforce least privilege
- Encrypt sensitive data across all states
- Implement secure software development practices
- Harden systems and ensure operational resilience

Detect: Monitoring for Anomalies and Incidents
Once protective controls are in place, institutions must actively monitor for early signs of trouble. The Detect function includes the tools and procedures necessary to identify suspicious activity before it causes significant harm.
- Implement continuous system and network monitoring
- Log events and analyze anomalies
- Monitor for suspicious behavior within physical and virtual environments

Respond: Incident Management and Containment
Even well-defended institutions will face incidents. The Respond function outlines how to act when something goes wrong—rapid triage, effective communication, and timely remediation all help reduce damage and disruption.
- Validate and prioritize incidents through established triage workflows
- Communicate across teams and to external stakeholders
- Investigate root causes to prevent recurrence

Recover: Restoring Systems and Services
Recovery ensures institutions can return to business as usual after an incident. This function is about restoring trust and operational continuity—not just systems. It reinforces resilience at every level of the organization.
- Launch and manage disaster recovery plans with clear milestones
- Coordinate with internal departments and regulatory bodies as needed
- Restore operations while capturing and applying lessons learned

Extend: Managing Third-Party and Supply Chain Risk
No financial institution operates in a vacuum. Third-party vendors and service providers are critical partners, but they also introduce risk. The Extend function helps institutions manage external dependencies without sacrificing security.
- Conduct due diligence before onboarding third-party vendors
- Embed cybersecurity expectations into contracts and SLAs
- Monitor vendor performance and compliance over time
- Plan for vendor exit or breach scenarios
%201%20(1).svg)
%201.svg)
THE GOLD STANDARD INCybersecurity and Regulatory Compliance
Steps for Implementing the CRI Cyber Profile
Implementation of the CRI Profile begins with determining the institution's Impact Tier using the 9-question Tiering Questionnaire. Based on Tier assignment, institutions respond to a subset of the 318 diagnostic statements:
- Tier 1: 318 statements (full set)
- Tier 2: 311 statements
- Tier 3: 282 statements
- Tier 4: 208 statements

Assessment Response Categories and Documentation Tips
Each diagnostic statement is answered using one of eight standardized response categories. Documentation must show that the control is implemented effectively, operating consistently, and reviewed periodically.
Tips for Effective Implementation:
- Use current evidence: Supporting documentation should not exceed 12-15 months in age.
- Focus on effectiveness: Evidence should demonstrate operational reliability and not just tool installation.
- Track assessment challenges: Maintain logs of internal disagreements and how they were resolved.
- Regular updates: Profile responses should be reviewed after significant business or regulatory changes.
Institutions are encouraged to socialize the Profile with all key stakeholders, including management, legal, audit, and compliance, and to integrate results into board reporting and remediation planning workflows.
Why Financial Institutions Choose NETBankAudit
NETBankAudit specializes exclusively in GLBA/FFIEC IT regulatory audits and assessments for community financial institutions. Our dedicated focus ensures that community banks and credit unions receive the specialized expertise needed to achieve and maintain complete regulatory compliance.
Industry-Specific Expertise Unlike Other Providers:
- Accounting Firms Gap: Traditional accounting providers often lack the specialized technical and engineering expertise required for thorough IT regulatory audits
- Technical Firms Gap: Most IT companies don't possess the in-depth regulatory knowledge and audit expertise needed for GLBA/FFIEC compliance

True Independence in FFIEC IT Regulatory Audits
NETBankAudit maintains complete independence from other products and services, aligning with FFIEC IT Audit guidelines which state:
"Potential conflicts of interest may arise if the outsourced auditing firm performs IT Audit functions in addition to other audit services, such as: Providing the independent financial statement, or serving in an IT or management consulting capacity."
FFIEC IT Audits Booklet, Outsourcing Internal IT Audits section
NETBankAudit's Expert Team Advantage
Certified Security & Regulatory Professionals:
- Extensive community banking and credit union experience
- Advanced security engineering expertise
- Comprehensive regulatory knowledge
- 100% full-time employees—no subcontractors
- Industry-leading certifications (CISSP, CISA, and more)
- Complete background verification for all team members
Contact us today to strengthen your financial institution's GLBA/FFIEC compliance posture with NETBankAudit's specialized regulatory audit services.
.avif)

.svg)

.webp)

.webp)











.webp)



.webp)

%201.webp)
.webp)
%20(3).webp)


.webp)


%20Works.webp)


.webp)




.webp)
%20(1).webp)

.webp)










.webp)
.webp)

.webp)
.webp)
.webp)
.webp)
.webp)
.webp)
%201.svg)